Mastering Kubernetes from Scratch Part 16 - Understanding Kubernetes Authentication and Authorization
Introduction to Kubernetes Authentication and Authorization
Introduction
Although the terms authentication and authorization are often used interchangeably, there is a difference. Authentication refers to who you are, while authorization refers to what you can do.
This chapter explains how authentication works in Kubernetes, the different authentication methods available, and how users and service accounts authenticate with the cluster.
Kubernetes Authentication
Kubernetes does not have a built-in user management system. Instead, it delegates authentication to external systems. Authentication is required before a request can be authorized.
Types of Authentication
Kubernetes supports several authentication mechanisms for users and workloads.
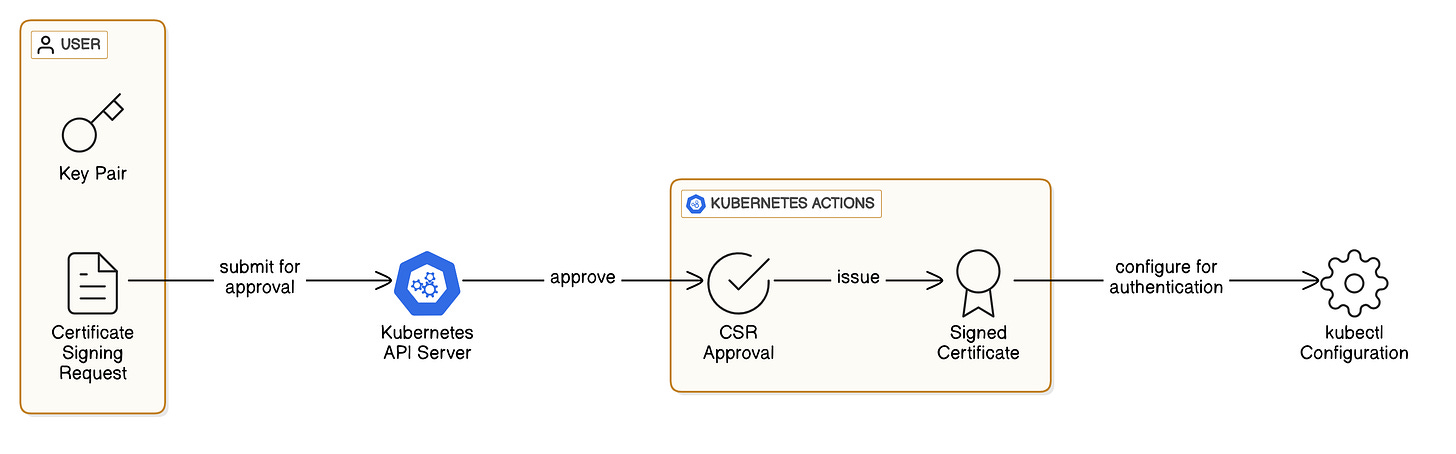
1. Client Certificates
Client certificates provide a secure authentication method where users and workloads present X.509 certificates to the API server. It requires generating a certificate signed by Kubernetes’ Certificate Authority (CA).
How it works:
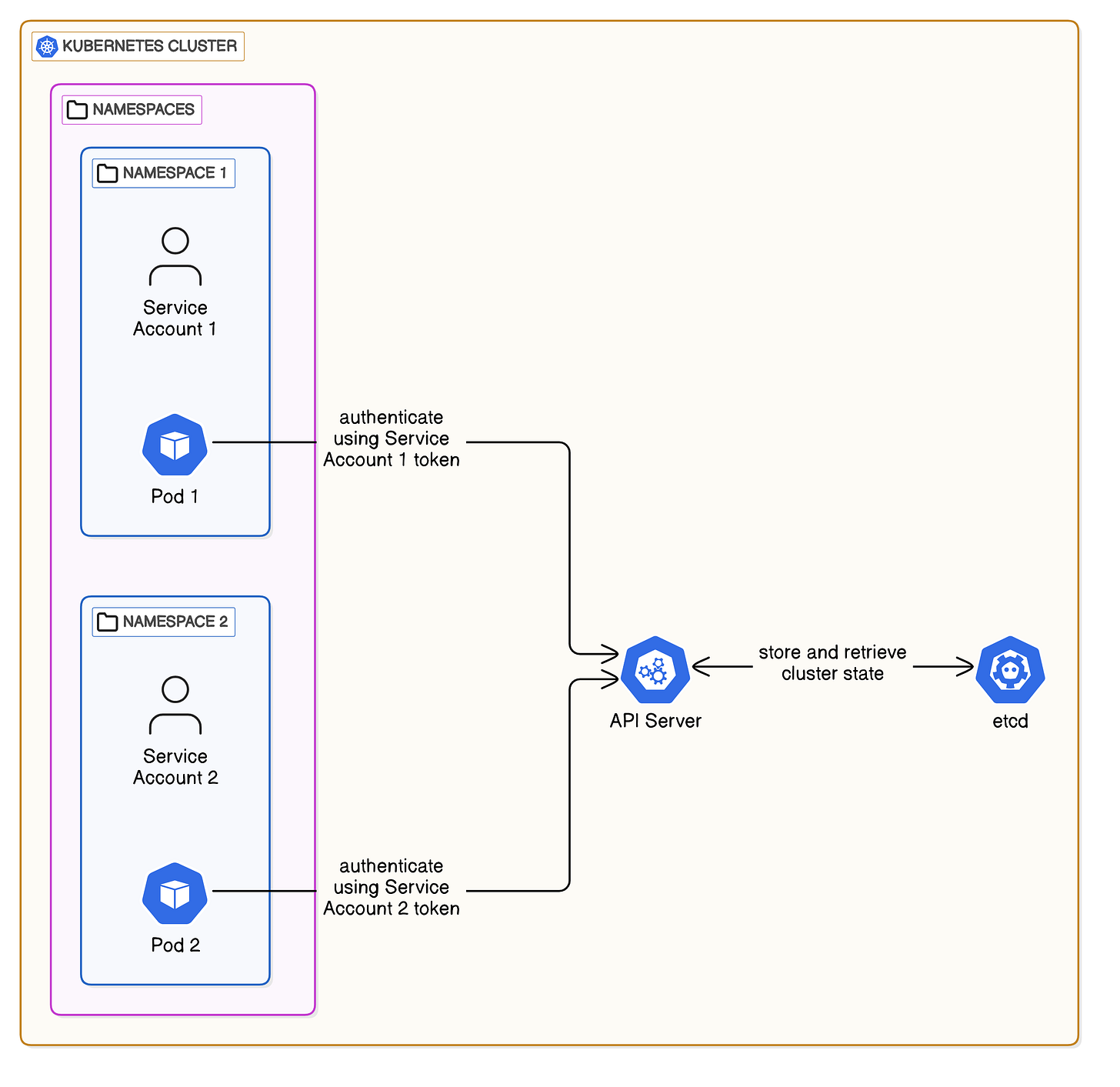
2. Service Accounts
A Service Account is a built-in Kubernetes authenticator that allows Pods to securely interact with the API server. Instead of using user credentials, Kubernetes automatically assigns Service Accounts to Pods and provides them with signed bearer tokens for authentication.
Key characteristics:
Every Pod gets a default service account unless specified otherwise.
Automatically time-bound tokens (since K8S v1.21).
Volume-projected tokens.
Automatic mounting controls.
Namespace-scoped identity.
Example ServiceAccount:
apiVersion: v1
kind: ServiceAccount
metadata:
name: app-service-account
namespace: production
automountServiceAccountToken: false # Security best practiceIf you enable token-projection, you can use this kind of configuration:
apiVersion: v1
kind: Pod
metadata:
name: app-pod
spec:
serviceAccountName: app-service-account
containers:
- name: app
image: app:1.0
volumes:
- name: service-account-token
projected:
sources:
- serviceAccountToken:
path: token
expirationSeconds: 3600
audience: "https://kubernetes.default.svc"How it works:
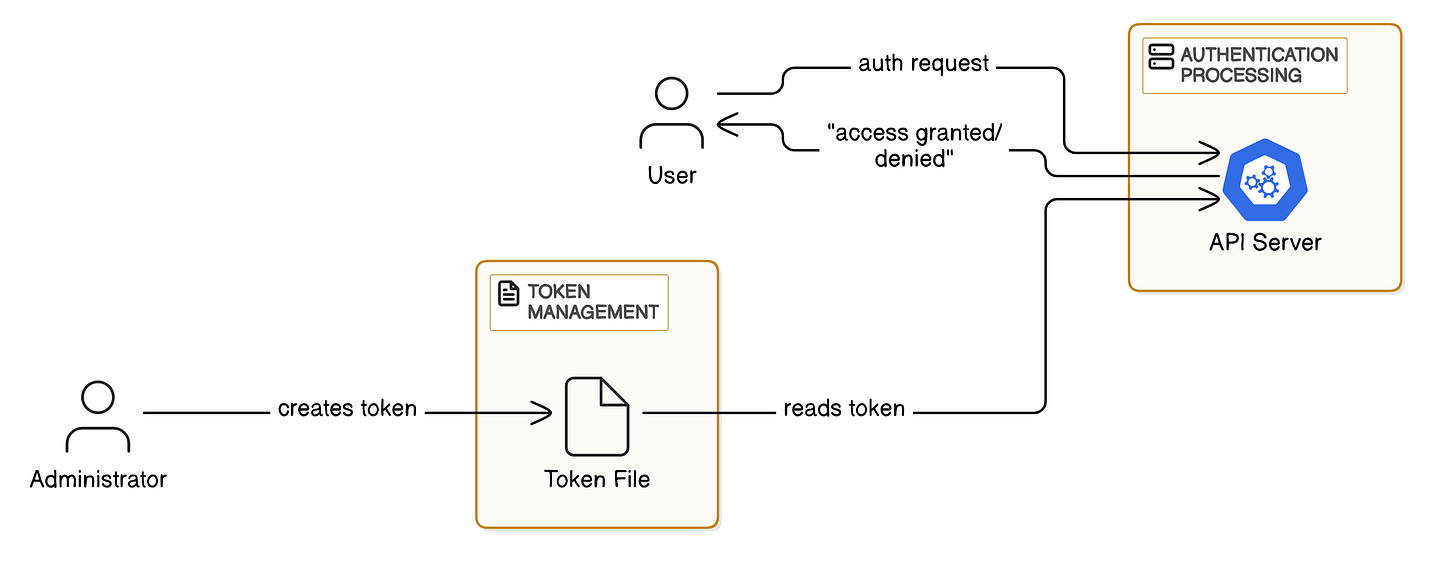
3. Static Token Files
Key characteristics:
Uses a predefined list of bearer tokens stored in a file.
Simple but not recommended for production due to security risks.
Tokens are static and need manual updates.
How it works:
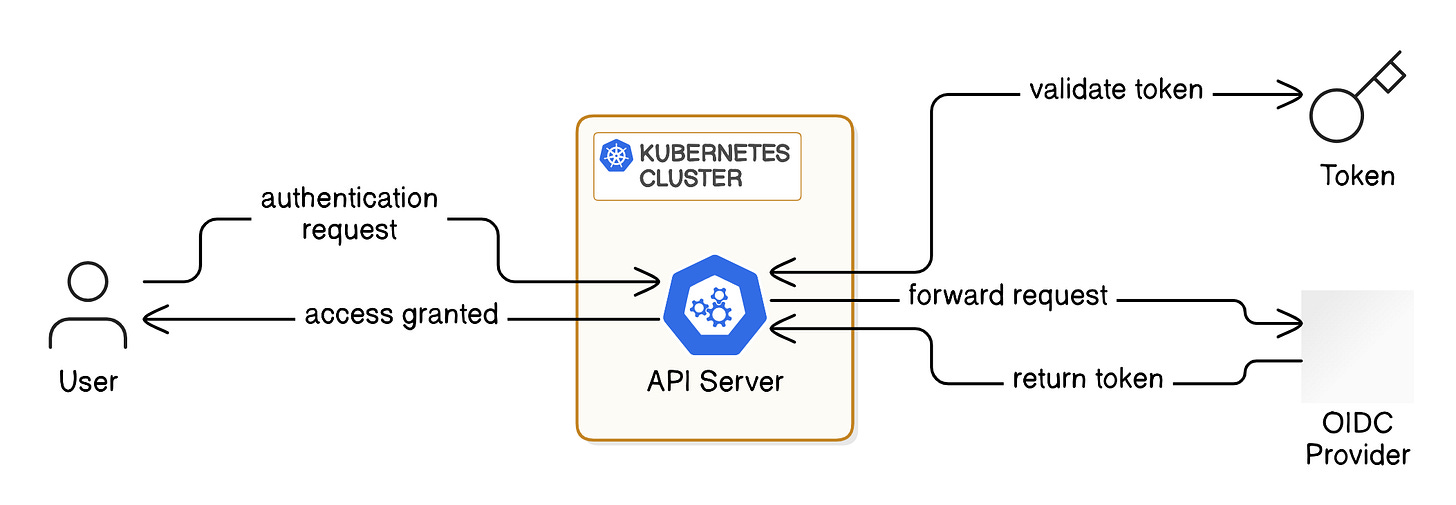
4. OpenID Connect (OIDC) Authentication
OIDC has become the preferred authentication method for enterprise environments, providing seamless integration with identity providers.
Key characteristics:
Enables single sign-on (SSO) using identity providers like Google, Okta, or AWS IAM.
Best option for enterprise environments.
Users authenticate via their external identity provider, which issues a token Kubernetes validates.
Example API Server Configuration:
--oidc-issuer-url=https://accounts.google.com
--oidc-client-id=kubernetes
--oidc-username-claim=email
--oidc-groups-claim=groupsHow it works:
5. Authentication via External Providers
You can integrate Kubernetes with external authentication providers like:
LDAP (Lightweight Directory Access Protocol) – Centralized authentication for enterprises.
OAuth – Used for API authentication (e.g., GitHub, Google).
Cloud Provider IAM – AWS IAM, Azure AD, or GCP IAM manage Kubernetes users.
6. Webhook Authentication
It is a specific Kubernetes authentication method where the API server calls an external HTTP/HTTPS service to verify bearer tokens. It enables custom authentication logic through an external service.
Example Webhook configuration:
apiVersion: v1
kind: Config
preferences: {}
clusters:
- name: webhook
cluster:
server: https://authn.example.com/authenticate
users:
- name: webhook
user:
client-certificate: /path/to/cert.pem
current-context: webhookKubernetes Authorization
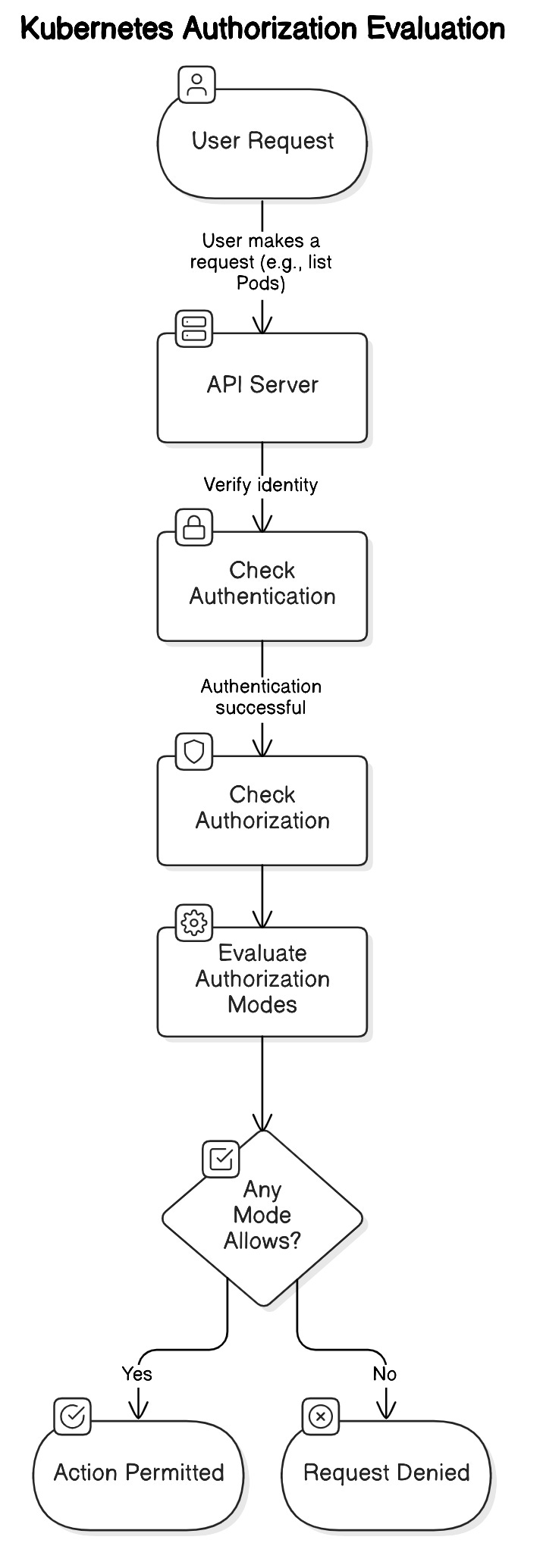
Once a user, service account, or node is authenticated, Kubernetes must decide what actions they are allowed to perform. This process is called authorization. Kubernetes uses multiple authorization modes to enforce access control policies.
Authorization Modes in Kubernetes
Keep reading with a 7-day free trial
Subscribe to Curious Devs Corner to keep reading this post and get 7 days of free access to the full post archives.